Gain comprehensive visibility and control of your security posture, including configurations, coverage, asset risks, and compliance, with real-time assessments and optimizations platform crafted for CISOs

Assess, benchmark and optimize security controls across EDR, SASE, Email, SIEM, IAM, Vulnerability management and other tools.
Comprehensive view of your security posture covering configurations, tool coverage, compliance, user/device risks and more.
Identify and manage risky users and devices with real-time assessments, risk scores, and no-code remediation workflows.
The Discern platform seamlessly integrates with your complete array of security products, establishing a baseline for your security controls and threat response through real-time health checks. We meticulously score and align your controls with industry frameworks such as MITRE, CIS, and NIST, ensuring compliance and demonstrating ROI. Leveraging advanced generative AI, we address your crucial security related queries, delivering tailored recommendations to meet your specific needs.
Learn More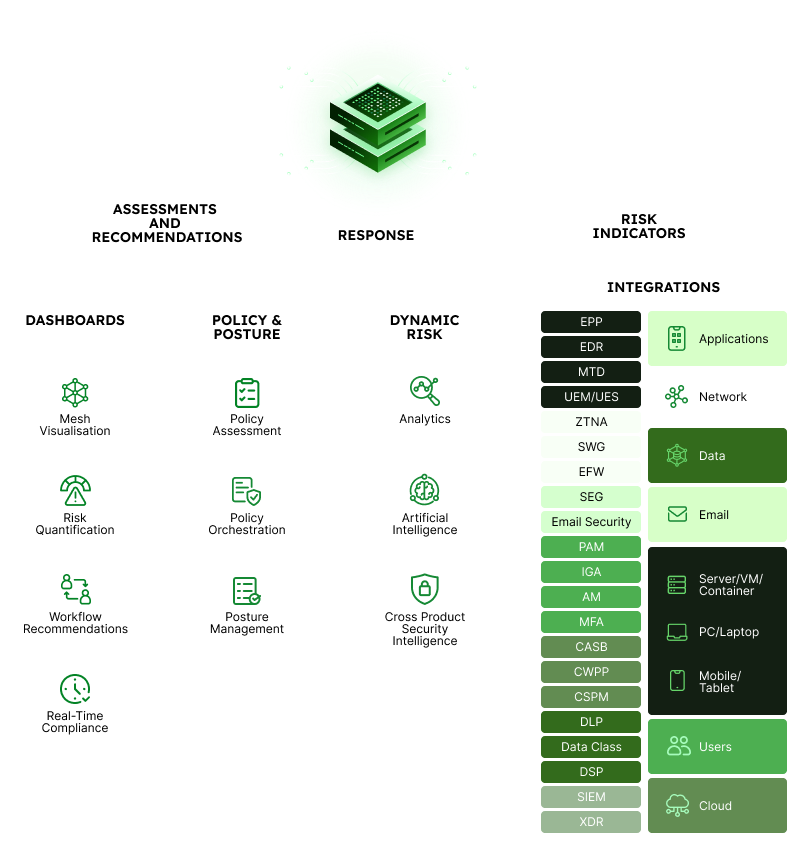
Discern creates a cybersecurity mesh across all your security tools, ensuring 360° visibility with real-time optimization of all security controls, resulting in proactive threat mitigation.
Increase utilization of available controls by 60%
Reduce spend on security controls assessment and management by 25%
Increase coverage in MITRE, CIS framework by 50%
Focus on 5% of users who account for 80% risks
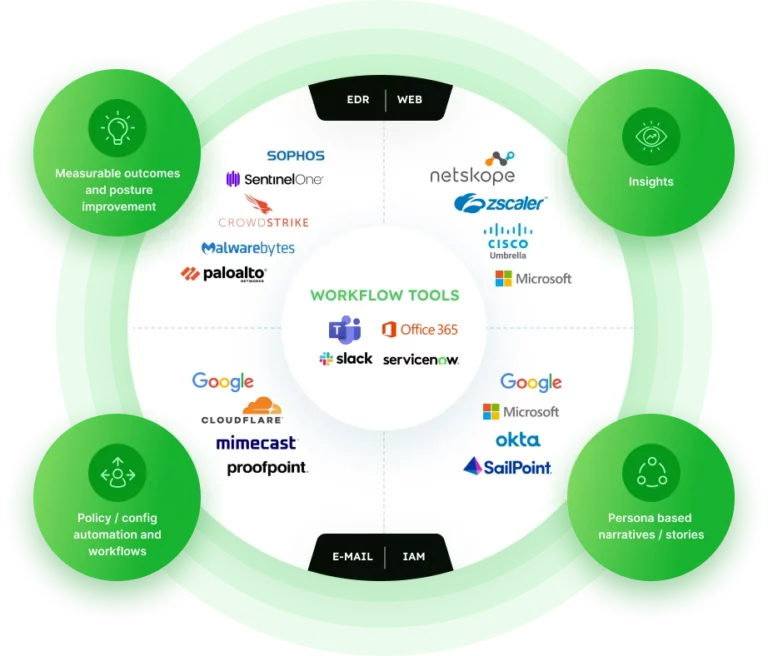
Our Virtuous Cycle: Insights, stories, policy automation and outcomes!
We strive to keep the equilibrium between productivity and security, so you have the most cost-effective security measures deployed.
Our automated workflows help you to :
Reduce redundancy, noise and boost utilization of existing security tools
Simplify compliance and re-configurations by triggering the right workflows
Take a balanced approach through solutions tailored to suit your toolkits of various security platforms
Assess, benchmark and optimize security controls across EDR, SASE, Email, SIEM, IAM, Vulnerability management and other tools.
Assess, benchmark and optimize security controls across EDR, SASE, Email, SIEM, IAM, Vulnerability management and other tools.
Assess, benchmark and optimize security controls across EDR, SASE, Email, SIEM, IAM, Vulnerability management and other tools.