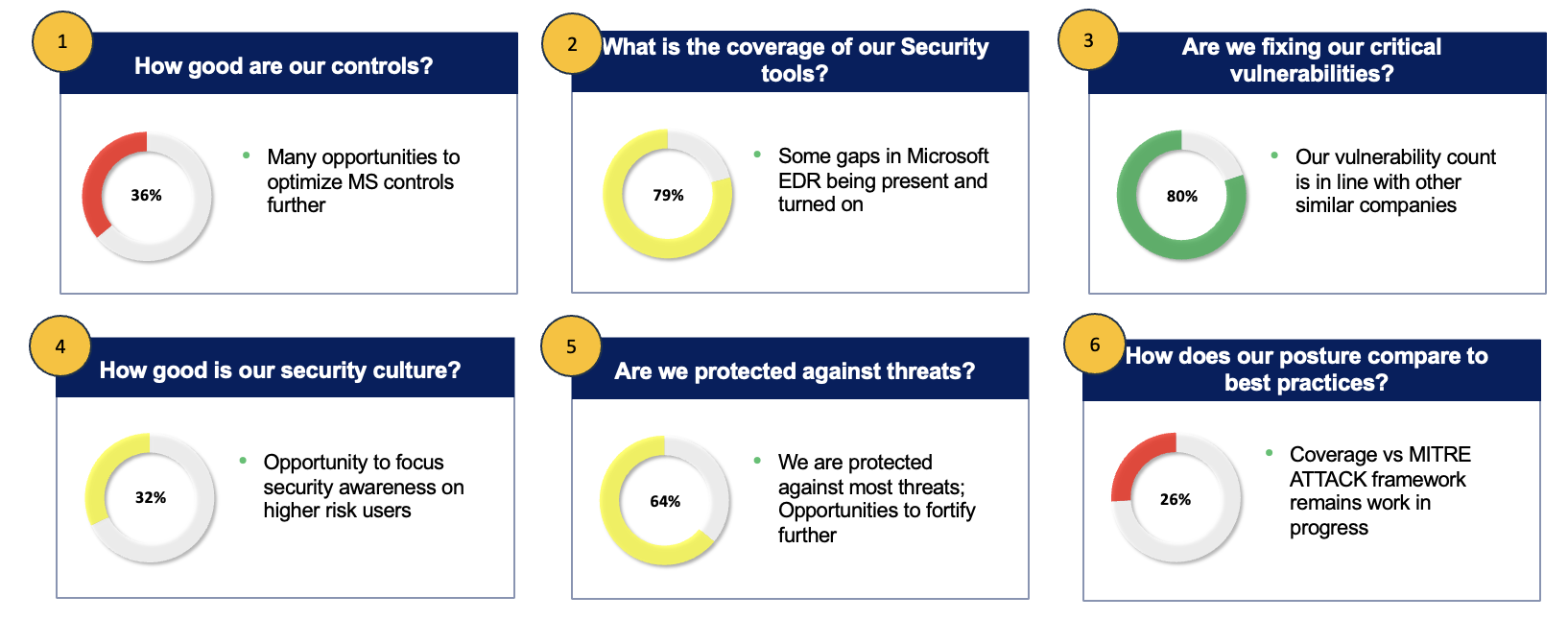
CISOs are often asked – are we truly secure by their executives and by their boards? In this paper, we lay out the building blocks that can help CISOs answer these questions. We will also describe AI led approaches that CISOs can leverage to answer these questions. As shown below, we believe there are 6 key building blocks that together help constitute a robust security posture.
Building block #1: Do we have the right controls in place in our organization?
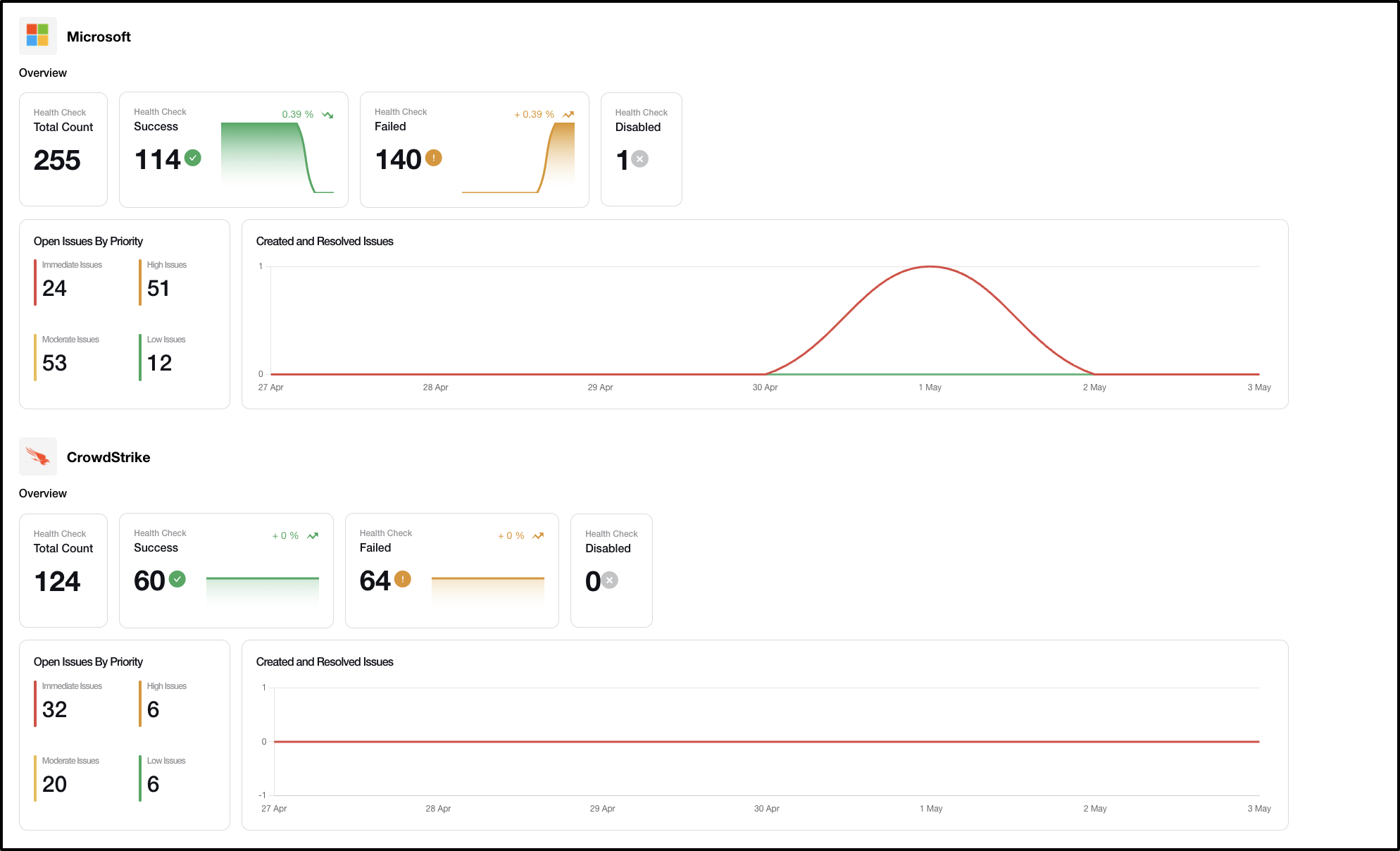
This is the first question CISOs often ask when they start their job. What controls do we have in place and how mature are we in terms of our controls? An organization is a multi-dimensional entity with people, devices, applications and interacts with the outside world through email, the world wide web, networks and through cloud services. As such, security controls are also multi-dimensional and the first step towards building a secure posture is to have the right controls in place across all the different dimensions of an organization. This involves looking at existing security products and seeing if the right controls are turned on and if the organization is making use of the features they are paying. It also involves looking at multiple dimensions and seeing if each dimension has the right controls (Devices – do they have ZTNA controls, humans- do they have MFA turned on etc.). With AI, it is now possible to learn an organizations posture leveraging APIs in a matter of minutes and compare it to best practices.
Building block #2: Are our controls deployed in all the right assets?
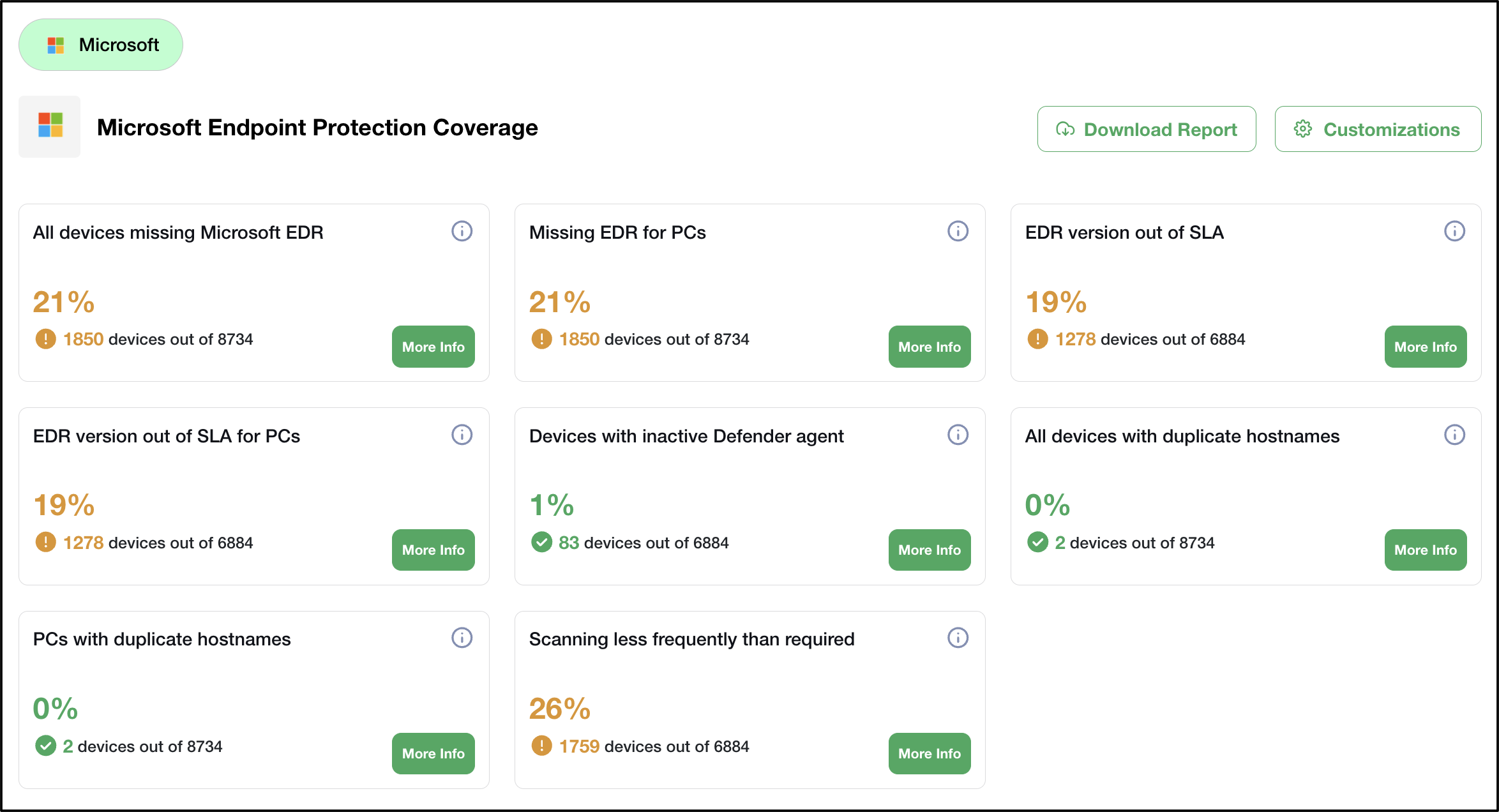
Multiple studies indicate that attacks begin with assets that are not protected. Assets can refer to devices or humans or applications. An important part of the cyber security's team is to discover all these assets and make sure they meet the company's "golden image" for cyber security. Often asset management is owned by IT and managed through tools like ServiceNow and security teams do not have full visibility into a company's assets and hence struggle to secure them. Further, in the pre AI age, asset management and asset inventories were wildly inaccurate. Now with AI, we can integrate with IT tools and cyber tools to have a much more accurate view of assets and also identify controls deployed in these assets. This in turn allows us to identify control gaps at an asset level. Further with AI, we can now build storylines on asset management with no manual intervention and this allows us to prioritize and plug asset security gaps.
Building block #3: Addressing the most critical vulnerabilities
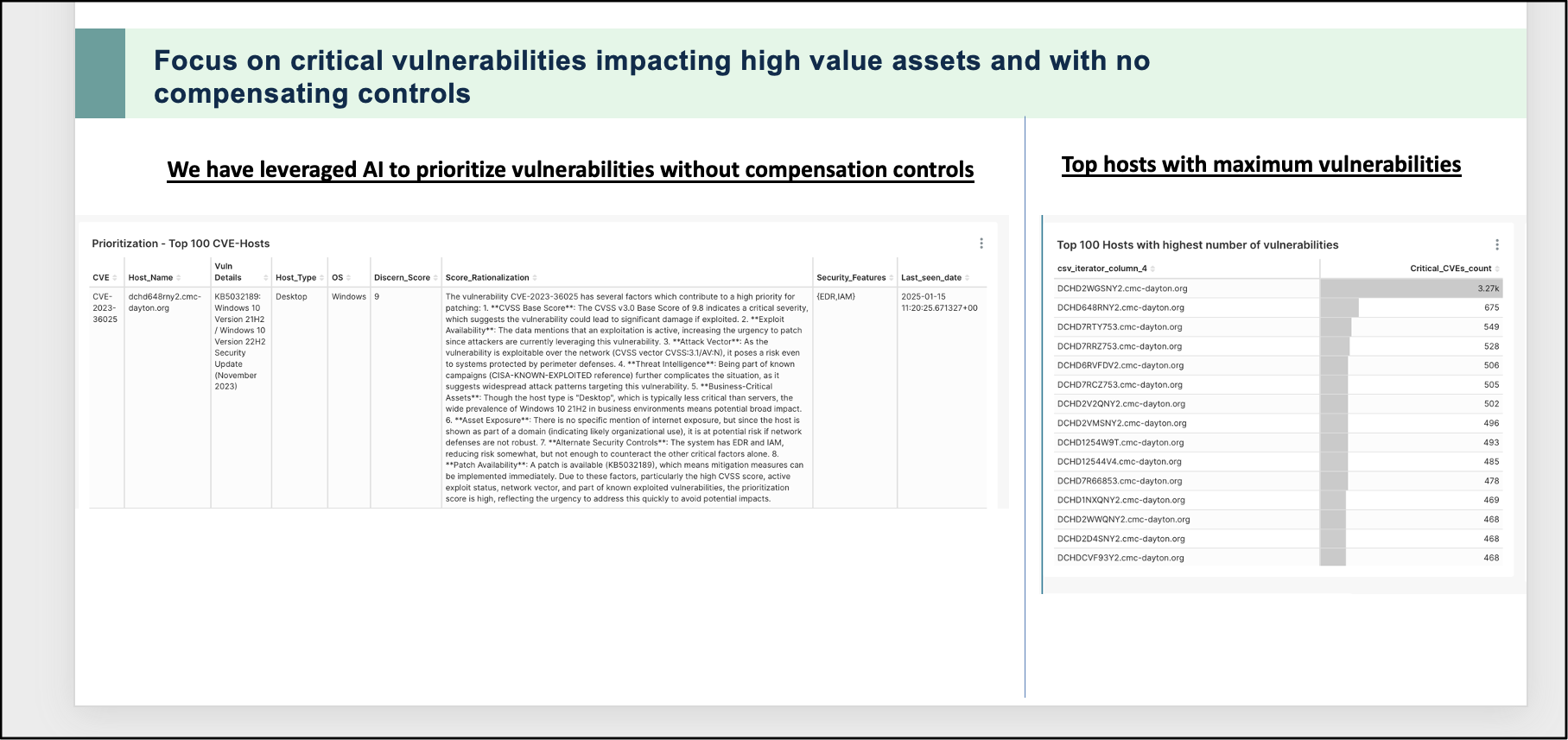
One of the problems that companies face is the overwhelming number of vulnerabilities (Patches, updates etc.) that they need to work on. A key element of making this manageable is to focus on vulnerabilities with known exploits impacting critical assets and with no compensating controls. Sizing the number of priority vulnerabilities and focusing efforts on the prioritized vulnerabilities is critical. We can now leverage AI to discover vulnerabilities with known exploits and then map them to the presence of compensating controls.
Building block 4: How secure is your culture?
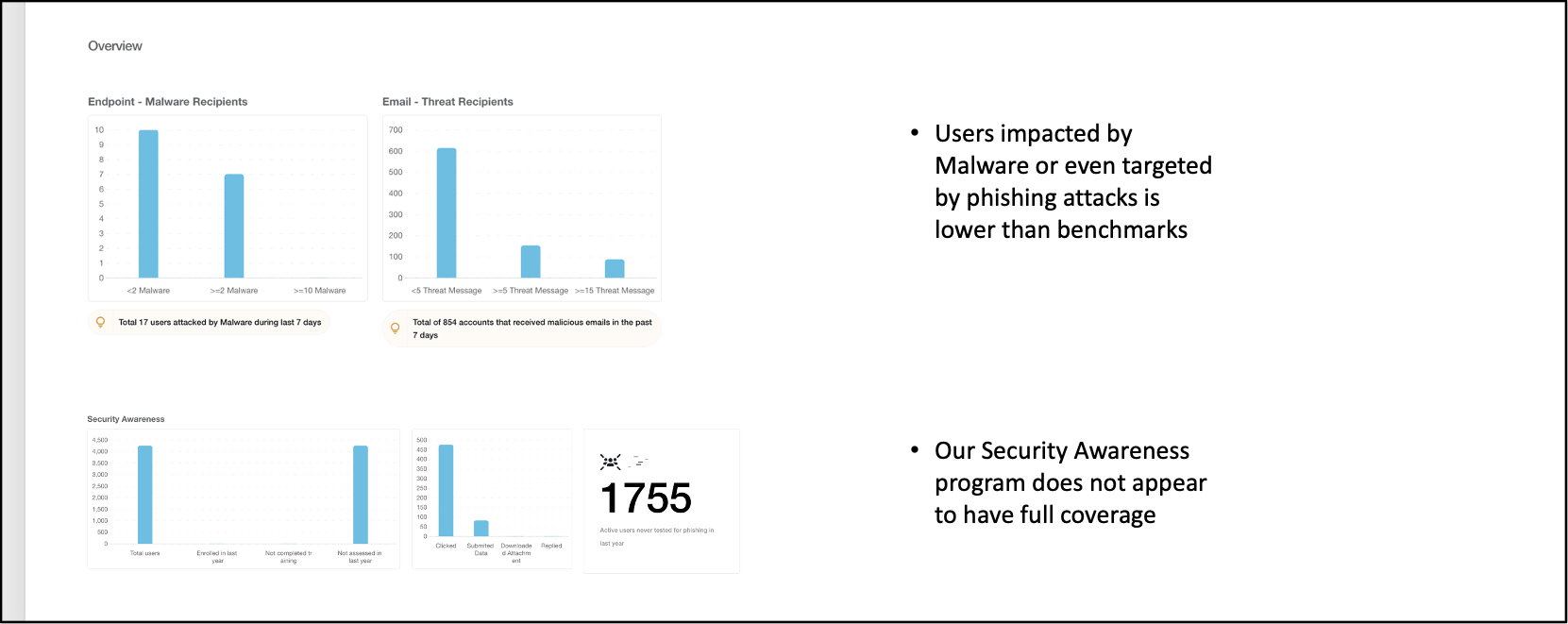
Multiple studies show human error is the #1 source of breaches. Therefore baselining how secure a company's culture is helps understand and baseline overall security posture too. To do this, multiple signals from different indicators of human behavior need to be gathered (ranging from most targeted users to users without MFA to users with excess permissions to users impacted by malware to users who have not completed their awareness training). With AI, it is now possible to aggregate multiple behavioral signals about each human and identify the most risky employees, esp. the most risky privileged employees.
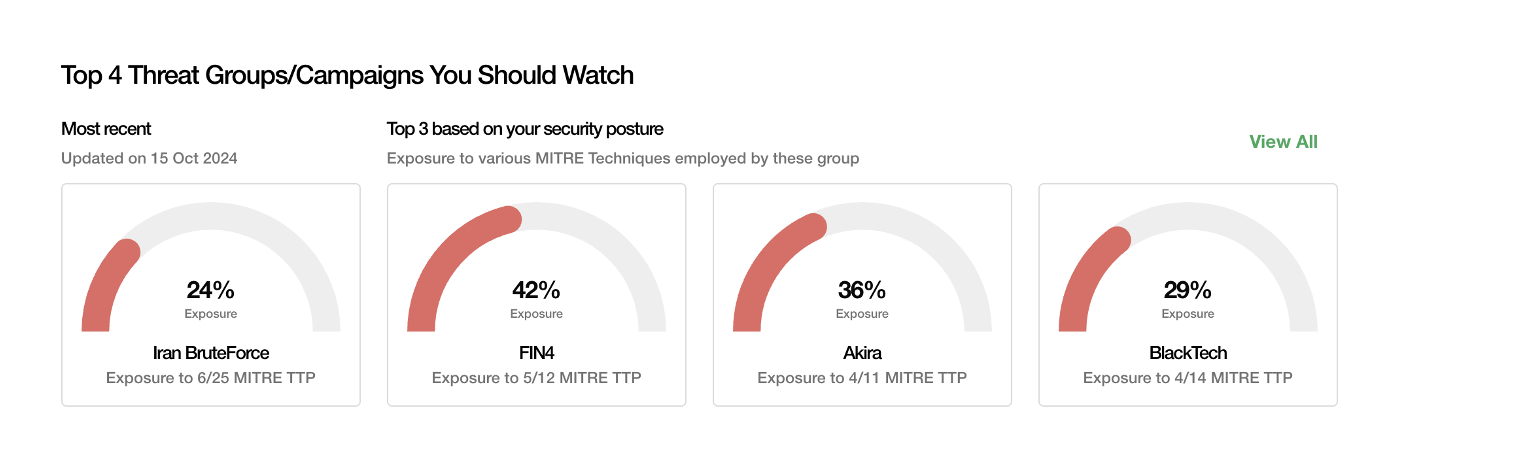
Building block #5: How exposed are we to the major threats impacting our industry today?
Posture can never truly be measured with just an inside out analysis. We also need to look at it outside – in using an attacker's lens. One proxy to do this is to simulate the latest threats impacting peer companies and seeing if our organization is indeed protected against these threats. Here we can leverage AI to marry the outside in analysis of threats to the inside out analysis of controls in place.
Building block #6: Where are we with respect to industry frameworks (MITRE, ZTA, NIST, CIS etc.)
Mapping and measuring our security posture to industry frameworks is another way to baseline the maturity of our overall security posture. The image below shows an organization's posture mapped to MITRE. Leveraging AI and LLMs makes it easy to build heat maps for multiple frameworks (MITRE, ZTA, NIST, CIS, HIPAA etc.)







