Discern Security is now SOC 2 Compliant
What is SOC 2 Compliance?
SOC 2 (Service Organization Control Type 2) compliance is a set of cybersecurity standards designed to help service organizations manage customer data based on five trust principles. Developed by the American Institute of Certified Public Accountants (AICPA), SOC 2 compliance is vital for organizations that handle customer data, ensuring that they adhere to strict information security policies and procedures.
There are two types of SOC 2 reports:
SOC 2 Type I: This report evaluates the design and implementation of a service organization's systems and controls at a specific point in time. It assesses whether the system and controls are suitably designed to meet the relevant trust principles.
SOC 2 Type II: This report examines the operational effectiveness of those systems and controls over a period, usually six months or more. It not only assesses the design but also the functioning and consistency of the controls.
What Does SOC 2 Certification Cover?
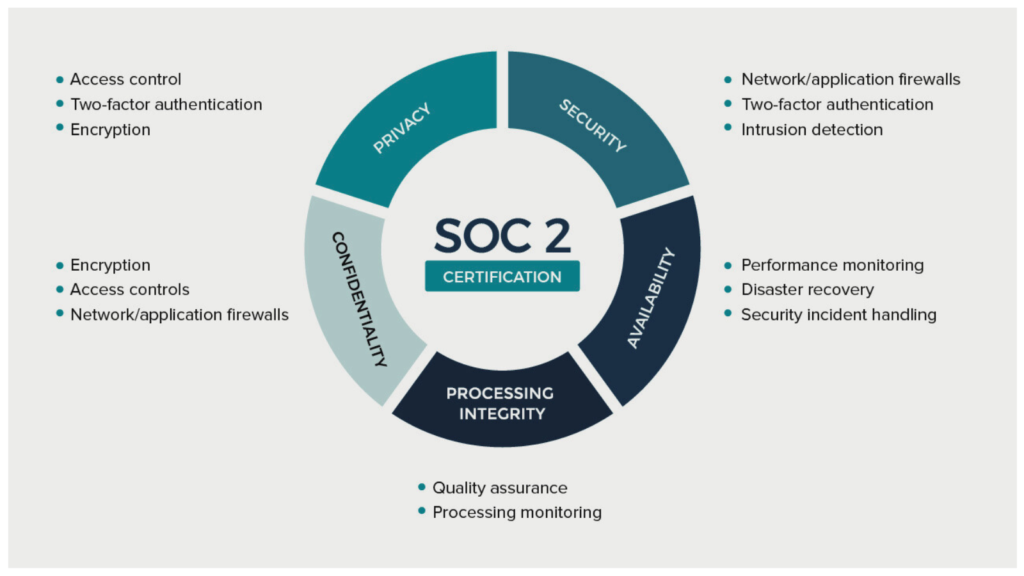
SOC 2 certification is based on five trust principles, each focusing on a different aspect of data security and management:
Security: The security principle ensures that the system is protected against unauthorized access (both physical and logical). It includes measures such as firewalls, intrusion detection, and multi-factor authentication to prevent data breaches and other security incidents.
Availability: This principle addresses whether the system is operational and accessible as stipulated by service level agreements (SLAs). It involves maintaining a reliable infrastructure, ensuring network performance, and providing adequate disaster recovery plans.
Processing Integrity: The processing integrity principle ensures that the system processing is complete, valid, accurate, timely, and authorized. It focuses on data processing controls to ensure that the data is processed correctly and consistently.
Confidentiality: This principle deals with the protection of confidential information. Controls are in place to restrict access to data to authorized personnel only and ensure that sensitive information is adequately protected.
Privacy: The privacy principle addresses the system's collection, use, retention, disclosure, and disposal of personal information. It ensures that personal data is handled in accordance with the organization's privacy notice and relevant privacy laws and regulations.
Why is SOC 2 Compliance Important for Organizations?
Achieving SOC 2 compliance is a significant accomplishment for any organization, as it demonstrates a strong commitment to data security and privacy. Here are some key reasons why SOC 2 compliance is crucial:
- Builds Trust with Clients: SOC 2 compliance provides assurance to clients that their data is handled with the utmost care and protected against unauthorized access and breaches. This trust is vital for maintaining and growing client relationships.
- Enhances Security Posture: The rigorous assessment and continuous monitoring required for SOC 2 compliance help organizations identify and address vulnerabilities, thereby enhancing their overall security posture. This proactive approach to security is essential in today's threat landscape.
- Ensures Regulatory Compliance: Many industries have stringent regulatory requirements regarding data protection and privacy. SOC 2 compliance helps organizations meet these requirements, thereby avoiding potential fines and legal issues.
- Improves Operational Efficiency: SOC 2 compliance involves the implementation of structured processes and controls, which can lead to improved operational efficiency. Streamlined procedures and clear guidelines help ensure that security practices are consistently followed.
- Competitive Advantage: In a competitive market, SOC 2 compliance can serve as a differentiator. It signals to potential clients that the organization is committed to high standards of security and data management, which can be a deciding factor in choosing a service provider.
- Reduces Risk: By adhering to SOC 2 standards, organizations can significantly reduce the risk of data breaches, operational disruptions, and reputational damage. Effective controls and continuous monitoring ensure that any issues are promptly identified and addressed.
Discern Security CISO, Vinay Srinivas elaborates –
" As a company, we have always strived to meet the highest standards, prioritizing security in everything we do. Undertaking the SOC 2 audit was crucial for us to benchmark and validate our security efforts. We are proud that our diligent approach has led us to achieve this esteemed certification. "
At Discern Security, achieving SOC 2 compliance is more than just a certification; it is a testament to our dedication to excellence and our unwavering commitment to safeguarding our clients' data. We are proud of this achievement and remain focused on maintaining the highest standards of security and service delivery.
Thank you for trusting Discern Security with your security needs. We look forward to continuing to provide you with unparalleled service and protection.





